According to a 2009 report by the World Bank, Yemen has “world-class deposits” of gold, and the World Bank is “surprised” that the country hasn’t been mined much for gold. Al Hariqah gold mine in Hajjah, Yemen, has proven gold deposits worth over 5 billion at today’s gold prices and could produce 200,000 ounces annually. … Continue reading How the IMF & World Bank Destroyed Yemen
Will the New Peace Deal Finally End the Conflict in Yemen?
For anyone following the conflict in Yemen, the news about a new peace being made will sound like a broken record, but there is genuine optimism about the truce that has been hashed out over the last month in Yemen. At the end of December last year, I wrote an article about an Omani delegation landing in Sanaa that … Continue reading Will the New Peace Deal Finally End the Conflict in Yemen?
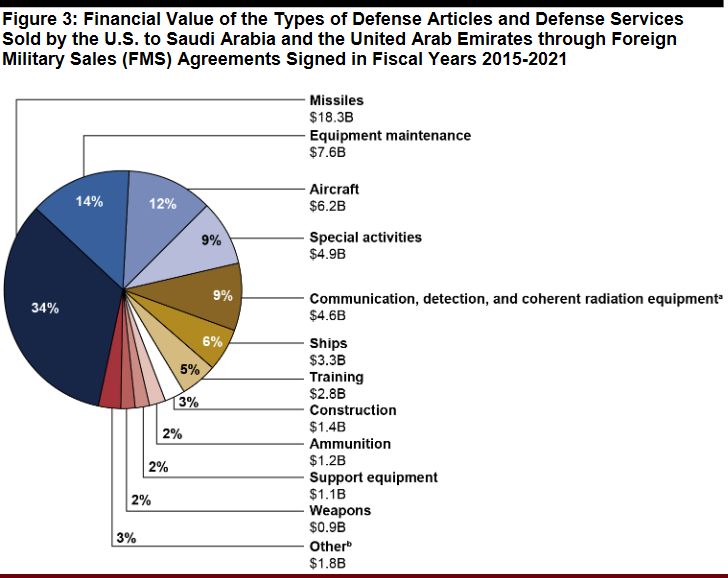
The US is Making Billions Being Warlords in Yemen
One of Biden's promises during his presidential campaign was to immediately move to end all support for the Saudi-led coalition's war in Yemen. In February 2021, Biden stood at a podium at the State Department and proclaimed that the war in Yemen must end. Biden underlined the humanitarian crisis as the key reason the United States withdrew … Continue reading The US is Making Billions Being Warlords in Yemen
The US claims the war in Yemen is for helping the Yemenis, but the reality is, its for America’s interest
The coalition war on Yemen at its beginning is for helping the Yemenis, but the reality is for America's interests: By Mohammed Albokhety Since the beginning of the war on Yemen, the countries of the coalition led by the United States claim that the war is to help the Yemenis and confront the Houthis who … Continue reading The US claims the war in Yemen is for helping the Yemenis, but the reality is, its for America’s interest
Top Israeli Intel Official Admits: “We failed to quell the Lions Den’s motive to fight”
Members of the Lions' Den marched through the West Bank Askar refugee camp in Nablus in an armed military parade in early December last year. Two months earlier, the Israeli Prime Minister brushed the group off as only having 30 members and being disorganized, vowing to "get his hands on them." Israel proclaimed the Lion's Den was defeated after … Continue reading Top Israeli Intel Official Admits: “We failed to quell the Lions Den’s motive to fight”
Ansar Allah Want Civil Servants Salaries Reinstated Before Resuming Peace Talks
According to video evidence and multiple outlets in the Middle East, Oman sent a delegation to Yemen this week in an effort to reignite peace talks between Saudi Arabia and Ansar Allah. Ansar Allah has been the governing power in Yemen since taking Yemen's capital city of Saana in 2015. Global powers paraded Mansour Hadi … Continue reading Ansar Allah Want Civil Servants Salaries Reinstated Before Resuming Peace Talks
History of Yemen Part 1
Yemen is a geopolitically important country and has been ever since a spice trade post in South Arabia evolved into a crucial biblical city we know today as Sanaa. The name Yemen is believed to come from its proximity to Mecca and Medina and is derived from the Arabic word "yamin." Yamin means "to the … Continue reading History of Yemen Part 1
You don’t need to be a far right or left to belong to Fascist league –The reality show
The 14 Fascist trades1- The Cult of Tradition; Nationalism, Flags, Slogans, Change is Bad, Harkening Back to an Ideal that Never Existed.2- The Rejection of Modernism; Industrial Machine is Proof of Power, Enlightenment is Depraved!3- The Cult of Action for Action's Sake; Cancel Culture, Thinking-Reasoning-Reflection is Weakness.4- Disagreement is Treason; Elimination of Political Enemies, Denial … Continue reading You don’t need to be a far right or left to belong to Fascist league –The reality show
The Truce in Yemen Holds as Air and Drone Strikes Fall by 78%
The truce in Yemen has held firm and has been extended despite accusations of violations by all sides. The warring parties have met every month since April of this year, and they met in early August to extend the truce in Yemen for two more months. According to the Armed Conflict Location & Event Data Project in … Continue reading The Truce in Yemen Holds as Air and Drone Strikes Fall by 78%
Peace isn’t a profitable business or part of the WEF partners interests
The people are used as funders of business that causes loss of lives everywhere. We have the right to refuse! It’s a human right to refuse funding the military industry and alliance like NATO, who’s whole existence is based on killing people in other countries. In some countries, where the military service is compulsory, they … Continue reading Peace isn’t a profitable business or part of the WEF partners interests